A Deep Dive into Network Communication
6 min read · Jun 1, 2024
Introduction: The OSI (Open Systems
Interconnection) model serves as a fundamental framework for understanding the
intricacies of network communication. Comprising seven distinct layers, each with its
unique functions and protocols, the OSI model delineates the journey of data as it
traverses through interconnected systems. In this detailed exploration, we delve into
each layer, uncovering its purpose, associated protocols, common threats, and strategies
for defense.
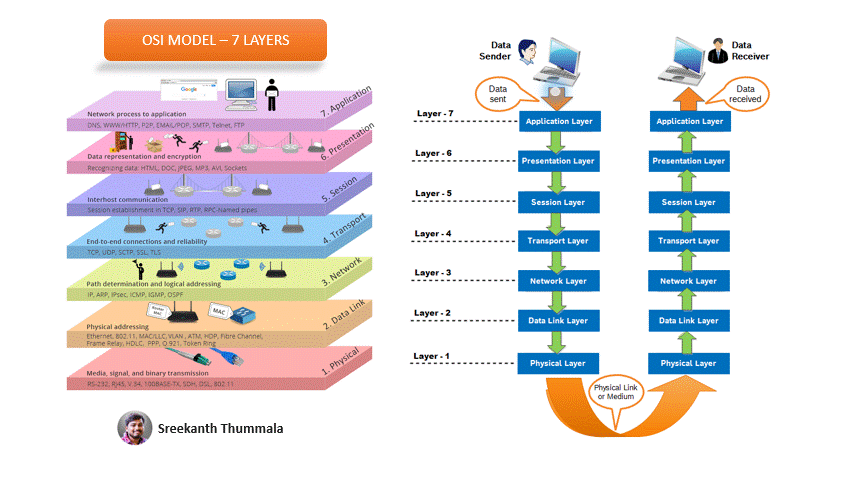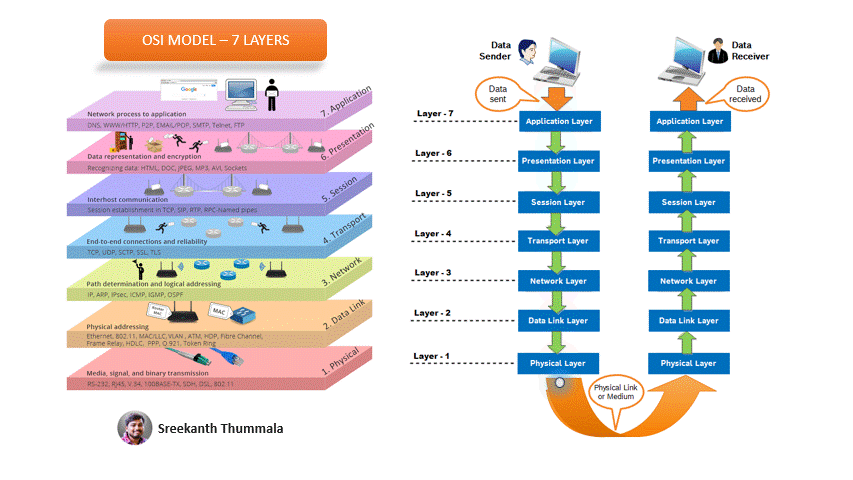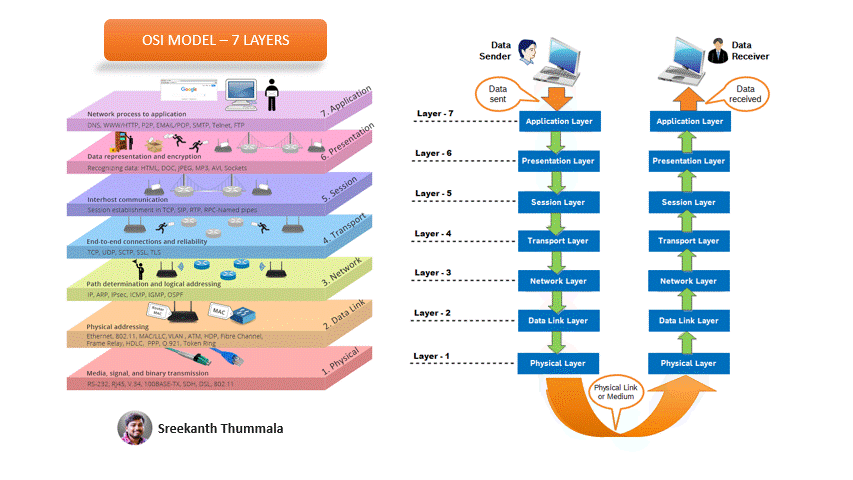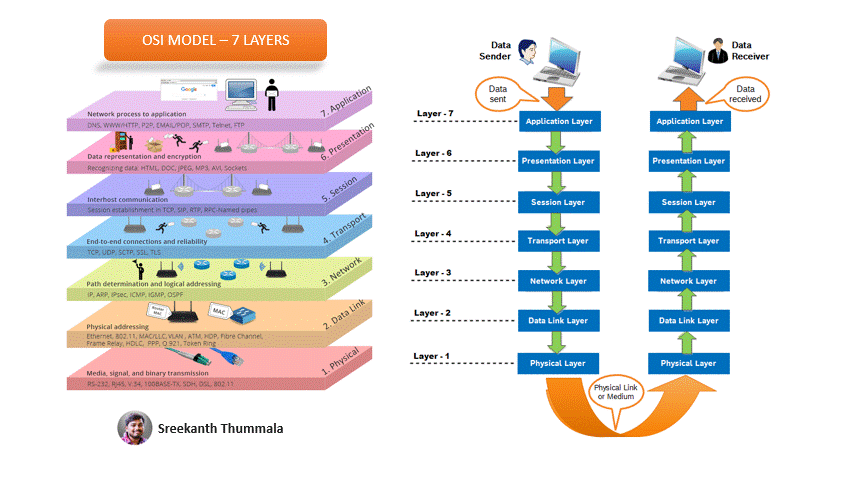
Layer 1: Physical Layer
Function: The Physical Layer establishes and maintains the physical connection between devices, defining the hardware specifications and transmission medium characteristics.
Protocols: Ethernet, Wi-Fi, Bluetooth, and fiber optic standards.
Common Threats: Physical tampering, cable tapping, electromagnetic interference.
Defense Strategies: Implement physical security measures, use shielded cables, employ encryption for wireless communication.
Layer 2: Data Link Layer
Function: The Data Link Layer ensures reliable data transfer between adjacent network nodes, managing access to the transmission medium and detecting errors in transmitted frames.
Protocols: Ethernet (IEEE 802.3), Wi-Fi (IEEE 802.11), Point-to-Point Protocol (PPP).
Common Threats: MAC address spoofing, ARP spoofing, switch flooding.
Defense Strategies: Enable port security, implement MAC address filtering, use VLANs for network segmentation.
Layer 3: Network Layer
Function: The Network Layer facilitates packet forwarding and routing, enabling communication between devices across different networks. It assigns logical addresses and determines the optimal path for data transmission.
Protocols: IP (Internet Protocol), ICMP (Internet Control Message Protocol), ARP (Address Resolution Protocol).
Common Threats: IP spoofing, smurf attacks, routing table manipulation.
Defense Strategies: Use network segmentation, implement access control lists (ACLs), enable ingress and egress filtering.
Layer 4: Transport Layer
Function: The Transport Layer ensures reliable end-to-end data delivery, providing mechanisms for error detection, flow control, and multiplexing of multiple connections.
Protocols: TCP (Transmission Control Protocol), UDP (User Datagram Protocol).
Common Threats: SYN flood attacks, UDP floods, session hijacking.
Defense Strategies: Implement SYN cookies, use rate limiting for UDP traffic, employ session encryption.
Layer 5: Session Layer
Function: The Session Layer manages and synchronizes communication sessions between applications, facilitating the establishment, maintenance, and termination of connections.
Protocols: NetBIOS (Network Basic Input/Output System), PPTP (Point-to-Point Tunneling Protocol).
Common Threats: Session replay attacks, man-in-the-middle attacks, session fixation.
Defense Strategies: Utilize session tokens, implement secure session management practices, enable session encryption.
Layer 6: Presentation Layer
Function: The Presentation Layer focuses on data representation and translation, ensuring that data exchanged between systems is in a format that can be understood by the recipient.
Protocols: SSL/TLS (Secure Sockets Layer/Transport Layer Security), ASCII (American Standard Code for Information Interchange).
Common Threats: SQL injection, cross-site scripting (XSS), data tampering during encryption.
Defense Strategies: Employ parameterized queries, validate input data, use secure encryption algorithms.
Layer 7: Application Layer
Function: The Application Layer provides interfaces for user applications and services, enabling tasks such as email communication, web browsing, and file transfers.
Protocols: HTTP (Hypertext Transfer Protocol), FTP (File Transfer Protocol), SMTP (Simple Mail Transfer Protocol).
Common Threats: Malware attacks, phishing, DNS spoofing.
Defense Strategies: Implement endpoint security solutions, use multi-factor authentication, conduct regular security training.
Layer 8: The Forgotten Layer (Human Layer)
Function: The Human Layer represents the critical influence of human factors on network security. It encompasses user behavior, adherence to policies, awareness levels, and the decisions made by individuals interacting with the system.
Common Threats: Insider Threats: Malicious insiders or employees who intentionally compromise security for personal gain or other motives. Social Engineering Attacks: Techniques such as phishing, pretexting, and baiting that exploit human psychology to gain unauthorized access to sensitive information. Negligence: Unintentional errors or oversight by users, such as weak password practices, mishandling sensitive data, or falling victim to scams.
Defense Strategies: Cybersecurity Training and Awareness Programs: Regular training sessions and awareness campaigns to educate employees about the latest threats, safe practices, and the importance of cybersecurity. Enforce Security Policies and Procedures: Establish and strictly enforce comprehensive security policies and procedures. Ensure all employees are familiar with these policies and understand their roles and responsibilities in maintaining security. Regular Security Audits and Assessments: Conduct frequent audits and assessments to evaluate the effectiveness of security policies and identify potential weaknesses. Implement corrective actions based on the findings to continuously improve the security posture. Behavioral Analytics: Utilize behavioral analytics to monitor and detect abnormal user behavior that may indicate insider threats or compromised accounts. Strong Authentication Mechanisms: Implement multi-factor authentication (MFA) to ensure that users are who they claim to be, reducing the risk of unauthorized access due to compromised credentials.
By addressing the human element in cybersecurity, organizations can significantly reduce the risk of breaches and enhance the overall security of their networks. A well-informed and vigilant workforce is a crucial line of defense against cyber threats.
Conclusion: Understanding the OSI model and
its associated layers is essential for building robust network security defenses. By
comprehensively analyzing each layer, identifying potential threats, and
implementing appropriate defense mechanisms, organizations can mitigate risks and
safeguard their networks against evolving cyber threats. Moreover, recognizing the
critical role of human factors underscores the importance of fostering a culture of
cybersecurity awareness and accountability, ensuring that security measures remain
effective in an ever-changing threat landscape.
Future Outlook: Enhancing the OSI Model for Evolving Threats
As technology evolves and cyber threats become increasingly sophisticated, the question arises: Will the OSI model suffice in addressing future challenges, or do we need to augment it with additional layers? While the OSI model has served as a foundational framework for understanding network communication, its current structure may require adjustments to adequately address emerging threats. Here’s a prognosis for the future and potential enhancements to the OSI model:
Need for Additional Layers: With the proliferation of IoT (Internet of Things) devices and the advent of technologies like 5G and AI, the attack surface of networks is expanding exponentially. This expansion introduces new vulnerabilities that may not be adequately addressed within the existing OSI model layers. Emerging threats such as quantum computing-based attacks, AI-driven malware, and supply chain vulnerabilities underscore the need for a more comprehensive and adaptive security framework.
Proposed Enhancements: Integration of AI and Machine Learning Layers: A dedicated layer focused on AI-driven threat detection and response could enhance the OSI model’s ability to mitigate advanced threats. AI algorithms can analyze vast amounts of network data in real-time to identify anomalous behavior and proactively defend against cyber attacks. IoT Security Layer: Given the proliferation of IoT devices and their unique security challenges, the inclusion of a dedicated IoT security layer could address the specific requirements of securing interconnected smart devices. This layer would focus on authentication, encryption, and access control mechanisms tailored to IoT ecosystems. Supply Chain Security Layer: With supply chain attacks becoming increasingly prevalent, a dedicated layer focused on securing the digital supply chain could mitigate risks associated with third-party dependencies. This layer would incorporate mechanisms for verifying the integrity of software and hardware components throughout the supply chain lifecycle.
Importance of Layer Integration and Interoperability: While proposing additional layers, it’s crucial to ensure seamless integration and interoperability with existing OSI model layers. The new layers should complement and enhance the functionality of the existing model rather than introducing complexity or fragmentation. Standardization efforts and industry collaboration will be essential to develop consensus around the proposed enhancements and ensure widespread adoption across diverse network environments.
Human-Centric Considerations: As cyber threats continue to evolve, human factors remain paramount in maintaining effective security defenses. Therefore, any enhancements to the OSI model should also consider the human layer, focusing on cybersecurity awareness, training, and behavioral analytics to address insider threats and social engineering attacks.
Conclusion: In conclusion, while the OSI model
has provided a solid foundation for understanding network communication, adapting to
the evolving threat landscape requires continuous evolution and innovation. By
augmenting the OSI model with additional layers tailored to address emerging
threats, integrating advanced technologies such as AI and IoT security, and
prioritizing human-centric security measures, organizations can enhance their
resilience against cyber attacks and safeguard the integrity of their digital
infrastructure in the years to come.
May the firewall be with us -
Mark Krings