A Comprehensive Guide to Phishing
8 min read · Jun 25, 2024
Introduction: Phishing is a form of cyber attack that aims to steal sensitive information such as usernames, passwords, and credit card details by masquerading as a trustworthy entity in electronic communications. This article provides an in-depth exploration of phishing, including its mechanisms, prevalence, impact, and defense strategies. We also discuss the role of artificial intelligence in both perpetuating and combating phishing attacks.
What is Phishing?
Definition: Phishing involves tricking individuals into providing confidential information by pretending to be a legitimate organization or individual. The term is derived from "fishing" for information, with the "ph" replacing "f" to evoke the term "phreaking," an early form of hacking.
Phishing attacks typically occur through email, but can also happen via phone calls (vishing), text messages (smishing), and social media platforms. Attackers use social engineering tactics to create a sense of urgency or fear, prompting victims to disclose sensitive information or click on malicious links.
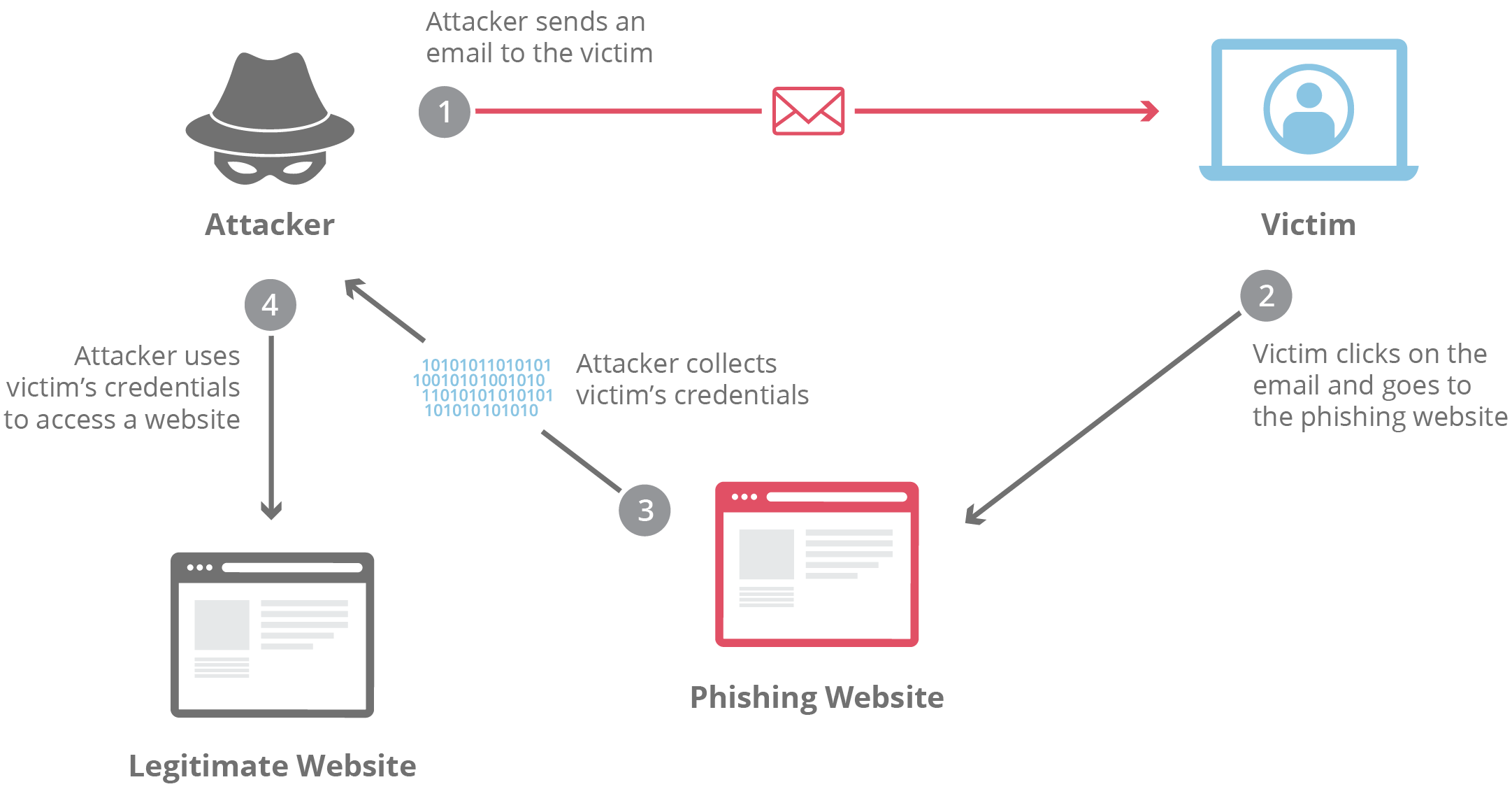
How Phishing Works
Email Phishing: Attackers send fraudulent emails that appear to come from reputable sources, such as banks, government agencies, or well-known companies. These emails often contain links to fake websites designed to steal login credentials or prompt users to download malware.
Spear Phishing: A more targeted form of phishing, where attackers customize their messages based on information they have gathered about the victim, such as their job role, interests, or recent activities. This increases the likelihood of the victim falling for the scam.
Clone Phishing: Attackers create a replica of a legitimate email that the victim has previously received, altering the original content to include malicious links or attachments. The altered email is then sent from a spoofed address, making it appear as though it came from the original sender.
Whaling: A type of spear phishing aimed at high-profile targets such as executives or celebrities. The goal is to gain access to sensitive information or large sums of money by exploiting the victim's authority and influence.
Prevalence of Phishing
Phishing is one of the most common cyber threats, affecting individuals and organizations worldwide. According to a report by the Anti-Phishing Working Group (APWG), there were over 1.5 million phishing attacks in 2023, a 20% increase from the previous year. This upward trend highlights the growing sophistication and persistence of phishing tactics.
Research by the cybersecurity firm Proofpoint indicates that 88% of organizations experienced a phishing attack in 2023. Furthermore, phishing remains the most prevalent initial access vector in data breaches, accounting for 36% of incidents, according to the Verizon Data Breach Investigations Report (DBIR) 2023.
Impact of Phishing
Financial Losses: Phishing attacks cause significant financial damage to individuals and organizations. The FBI's Internet Crime Complaint Center (IC3) reported that phishing scams led to over $2.7 billion in losses in 2023.
Data Breaches: Compromised credentials from phishing attacks can lead to data breaches, exposing sensitive information and causing reputational damage. In 2023, several high-profile data breaches, including those at major financial institutions and healthcare providers, were traced back to successful phishing campaigns.
Operational Disruption: Phishing attacks can disrupt business operations, especially when ransomware is involved. The downtime and recovery costs associated with such incidents can be substantial.
Psychological Impact: Victims of phishing may experience stress, anxiety, and a loss of trust in digital communications. This psychological toll can be particularly severe for those who fall prey to sophisticated scams.
How to Protect Against Phishing
Education and Awareness: Conduct regular training sessions to educate employees and individuals about phishing tactics and how to recognize suspicious emails and messages.
Email Filtering: Implement advanced email filtering solutions to detect and block phishing emails before they reach the inbox. These solutions can identify malicious links and attachments.
Multi-Factor Authentication (MFA): Use MFA to add an extra layer of security to accounts. Even if credentials are compromised, MFA can prevent unauthorized access.
Regular Software Updates: Keep software and systems updated to protect against vulnerabilities that phishing attacks may exploit.
Incident Response Plan: Develop and regularly update an incident response plan to quickly and effectively respond to phishing attacks. This plan should include steps for containment, eradication, and recovery.
Phishing and AI
AI-Powered Phishing Attacks: Cybercriminals are increasingly using AI to enhance the effectiveness of phishing attacks. AI can analyze large datasets to create highly personalized and convincing phishing emails. AI chatbots can also be used to engage with victims in real-time, increasing the likelihood of success.
AI for Phishing Detection: On the defensive side, AI is being used to detect and prevent phishing attacks. Machine learning algorithms can analyze email content, sender behavior, and other patterns to identify and block phishing attempts. AI can also enhance user training by simulating phishing attacks and providing real-time feedback.
The use of AI in phishing attacks is a double-edged sword. While AI enables cybercriminals to craft more sophisticated and targeted attacks, it also empowers cybersecurity professionals to develop advanced detection and prevention mechanisms. The ongoing battle between attackers and defenders highlights the importance of staying ahead with cutting-edge technology and continuous vigilance.
Case Studies
Case Study 1: The Twitter Hack of 2020: In July 2020, high-profile Twitter accounts, including those of Elon Musk, Barack Obama, and major companies like Apple and Uber, were compromised in a massive phishing attack. The attackers used social engineering tactics to gain access to Twitter's internal tools, ultimately tricking employees into providing their credentials. The breach resulted in a significant financial scam and widespread media coverage, underscoring the effectiveness and impact of well-executed phishing attacks.
Case Study 2: The Anthem Data Breach: In 2015, health insurance giant Anthem suffered a data breach that exposed the personal information of nearly 80 million individuals. The attack began with a phishing email that allowed the attackers to gain access to Anthem's network. This breach highlighted the vulnerabilities in the healthcare sector and the importance of robust phishing defenses.
Case Study 3: The Sony Pictures Hack: In 2014, Sony Pictures Entertainment was targeted in a high-profile cyber attack attributed to North Korean hackers. The attackers used spear phishing emails to compromise Sony's network, leading to the release of sensitive data and significant operational disruption. The incident illustrated the severe consequences of phishing in the corporate world and the need for comprehensive security measures.
Conclusion
Phishing remains one of the most pervasive and damaging cyber threats today. Its success lies in the exploitation of human vulnerabilities and the constant evolution of attack techniques. As phishing attacks become more sophisticated, leveraging technologies such as AI, the need for advanced defense strategies and heightened awareness becomes increasingly critical.
Protecting against phishing requires a multifaceted approach that includes education, technological defenses, and robust incident response plans. By understanding the mechanics of phishing, recognizing its prevalence and impact, and staying informed about the latest trends, individuals and organizations can better safeguard their sensitive information and maintain their cybersecurity posture.