Understanding Zero Trust in Cybersecurity
10 min read · Dec 20, 2024
Introduction: Zero Trust represents a paradigm shift in cybersecurity, aiming to enhance security by challenging the traditional "trusted network" model. In this model, organizations secure their perimeter and trust that everything inside is secure. Zero Trust, however, operates on the belief that there is no "trusted" zone - every device, user, and network must be continuously authenticated and validated, regardless of their location. This is based on the principle of "never trust, always verify," which involves scrutinizing access requests based on identity, device health, and contextual information. Zero Trust is not just a product but a comprehensive strategy that integrates across all areas of an organization's cybersecurity infrastructure to provide a unified and proactive defense. This model emerged in response to the increasing complexity and sophistication of cyber threats that traditional perimeter-based security models failed to address adequately.
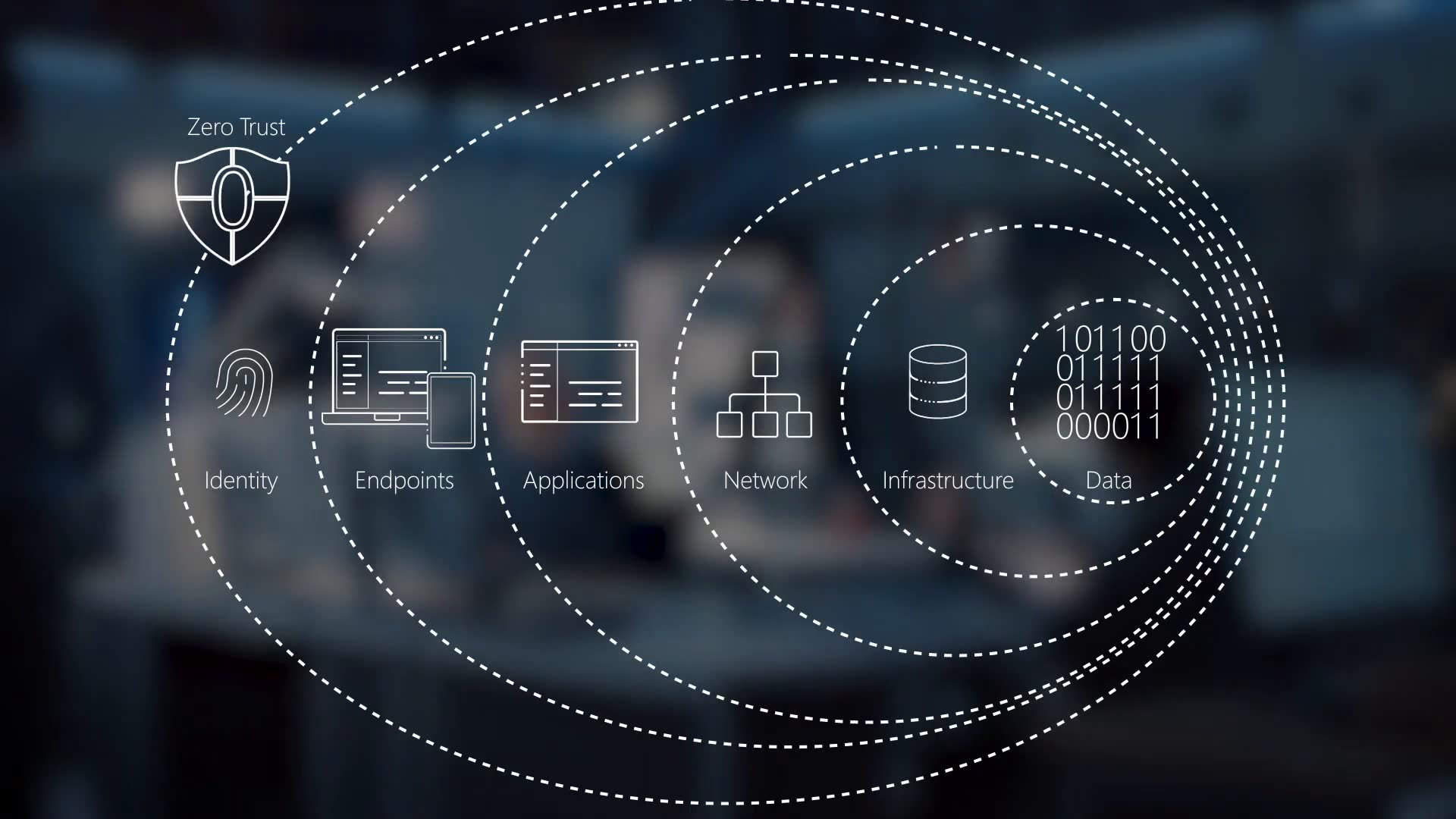
Core Principles of Zero Trust
1. Verify Identity: In a Zero Trust architecture, user identity is a critical component. Every access attempt is evaluated against a strong identity validation framework, such as multi-factor authentication (MFA), which requires users to provide multiple forms of verification (passwords, security tokens, biometrics) before access is granted. This ensures that only authorized users can access sensitive resources, even if they are inside the network. The principle of continuous verification also applies, where identity checks are performed not only during login but periodically as the session continues, adding another layer of protection.
2. Device Health Checks: In a Zero Trust environment, it`s not just the identity of the user that is verified but also the health of the device connecting to the network. Device health checks involve assessing if the device has up-to-date security features - like antivirus software, encryption settings, and patch levels - before it is allowed access to the network. If a device does not meet these criteria, access is denied, preventing potentially compromised devices from infiltrating the network. This concept of device health checks ensures that only devices that comply with the organization's security policies are allowed access.
3. Microsegmentation: Zero Trust uses microsegmentation as a key principle to protect against lateral movement of attackers. Microsegmentation divides the network into smaller, isolated segments, each protected by its own set of security policies. These segments act as security zones, making it much harder for an attacker who has breached one segment to move to another. Each segment’s security controls are tailored to the resources and data within it, limiting the attack surface. This segmentation not only improves security but also makes it easier to manage and monitor network traffic.
4. Least Privilege Access: Zero Trust promotes the principle of least privilege, which restricts access to only those resources necessary for a user or device to perform its role. Under this model, users are only given the minimum level of access required to perform their job functions. This reduces the risk of internal threats by minimizing the damage an unauthorized user can cause if they gain access to the system. Privileges are dynamically adjusted based on the user's role and the context of their request, ensuring that they are not granted more access than they need. Just-in-Time Access (JIT), where privileges are granted for the minimum time necessary, can further enhance security.
5. Continuous Monitoring and Analysis: Continuous monitoring is a hallmark of the Zero Trust model. In this model, all activities—whether successful or failed access attempts—are logged and monitored in real time. Security tools such as Security Information and Event Management (SIEM) systems are used to analyze this data for patterns, anomalies, or signs of an attack. This constant surveillance allows for early detection and response to threats, enabling security teams to isolate and mitigate incidents before they cause damage. Continuous monitoring is also crucial for adapting security policies and procedures to new threats and vulnerabilities. Additionally, incorporating User and Entity Behavior Analytics (UEBA) can further enhance the detection of anomalies in user behavior.
Implementing Zero Trust
1. Assessing Current State: The journey to implement Zero Trust starts with assessing the existing state of an organization's cybersecurity infrastructure. This includes reviewing current security policies, network architecture, and access controls. An understanding of what data and resources are most critical to the organization helps prioritize which parts of the network should be segmented first. This assessment also identifies existing gaps in security and areas that can be improved to align with Zero Trust principles.
2. Segmentation: Microsegmentation is a foundational step in implementing Zero Trust. Segregating the network into smaller, secure segments makes it harder for an attacker to move laterally across the network. Each segment should have its own security controls and monitoring processes tailored to the specific data and resources within it. Implementing microsegmentation requires careful planning to ensure that network traffic is monitored and segmented appropriately. This may involve deploying technologies such as Software-Defined Perimeter (SDP) to create dynamic boundaries around segments, making it harder for unauthorized devices to access resources.
3. Implementing Strong Identity Verification: To fully embrace Zero Trust, organizations must prioritize strong identity verification. This involves adopting multi-factor authentication (MFA) across all endpoints and systems to verify user identities rigorously. Additionally, advanced authentication methods like biometrics or single sign-on (SSO) can enhance security. Zero Trust principles require these identity checks to be continuously verified throughout the user session, adding another layer of security against identity theft and unauthorized access.
4. Monitoring and Logging: Continuous monitoring is critical to the success of Zero Trust. Security teams should deploy monitoring tools that can capture and analyze all access activities across the network. This includes not only monitoring for suspicious activities but also ensuring that data from different sources is integrated into a cohesive view, which can be fed into a SIEM system for further analysis. Monitoring and logging allow organizations to detect anomalies, identify security breaches, and respond promptly to incidents.
5. Educating and Training: Implementing Zero Trust also requires a cultural shift within the organization. Employees need to be educated about the importance of security, their role in protecting sensitive data, and the new protocols that come with Zero Trust. Regular training ensures that employees are aware of best practices for secure access, especially when working remotely or using personal devices. This cultural change also includes encouraging security-conscious behavior across the organization.
Challenges of Implementing Zero Trust
1. Complexity: One of the primary challenges of Zero Trust is its inherent complexity. Implementing Zero Trust requires significant changes to an organization's security architecture, access controls, and user behavior. The complexity is amplified if an organization has a diverse IT environment with different operating systems, networks, and devices. Managing the interplay between these elements while maintaining performance and user experience can be challenging.
2. Cost: Transitioning to a Zero Trust model can be costly. The investment required for new technologies, infrastructure changes, and employee training can be significant. Organizations may need to upgrade existing security tools, implement new solutions like SDP or advanced identity verification methods, and establish a robust SIEM system for monitoring. These costs need to be carefully managed, especially for smaller organizations with limited budgets.
3. Resistance to Change: Zero Trust represents a shift from traditional security models that many employees and management are accustomed to. The move to a Zero Trust model requires a cultural shift within the organization, with changes in policies, protocols, and user behavior. This can lead to resistance from employees who are used to existing practices and may find the new requirements cumbersome or inconvenient.
4. Legacy Systems: Many organizations still rely on outdated systems and applications that do not support the Zero Trust principles. Integrating these legacy systems into a Zero Trust framework can be challenging. These systems may not support advanced authentication methods, secure segmentation, or continuous monitoring. Overcoming these barriers often requires a significant investment in modernization, which can be prohibitive.
5. Scalability: As organizations grow, scaling Zero Trust can be challenging. Expanding segmentation, managing access controls for a larger user base, and maintaining consistent monitoring across a broader network all add complexity. Scalability issues often require organizations to re-evaluate their security architecture and may lead to compromises on the principles of Zero Trust.
Benefits of Adopting Zero Trust
1. Enhanced Security: One of the primary benefits of adopting Zero Trust is enhanced security. By requiring continuous verification for every access request, organizations are better protected against insider threats, external attacks, and data breaches. The concept of never trusting any device, user, or network reduces the attack surface significantly, making it more difficult for attackers to gain unauthorized access.
2. Improved Compliance: Zero Trust helps organizations meet compliance requirements, such as those set by GDPR, HIPAA, or CCPA. By controlling access strictly and monitoring all activities, Zero Trust ensures that sensitive data is protected, and unauthorized access is prevented. This adherence to compliance standards can mitigate the risk of penalties associated with data breaches and regulatory non-compliance.
3. Simplified Threat Detection and Response: Continuous monitoring under Zero Trust enables organizations to detect threats more quickly and respond to incidents in real-time. With a unified view of all activities across the network, security teams can identify suspicious behavior, isolate threats, and mitigate risks before they cause significant damage. This improved threat detection and response capability is a significant advantage for organizations.
4. Better User Experience: Zero Trust can lead to a better user experience. By implementing strict access controls only when needed, users experience fewer disruptions when accessing resources. This is especially important for remote work scenarios where users may access the network from various locations and devices. The principles of Zero Trust ensure that users have a seamless experience without sacrificing security.
5. Lower Total Cost of Ownership: While the initial implementation of Zero Trust can be costly, the long-term benefits can result in a lower total cost of ownership. Reduced risks of breaches, lower insurance premiums, and fewer remediation efforts mean that the overall cost of security can be minimized. Zero Trust can also reduce costs associated with compliance, fines, and reputational damage from breaches.
Conclusion
Zero Trust represents a significant shift in how organizations think about security. By focusing on identity, device health, and the principle of least privilege, organizations can protect themselves from both external and internal threats. Implementing Zero Trust is not just a technical change but a cultural shift that requires commitment from all levels of an organization. The challenges are significant, but the benefits—enhanced security, compliance, and lower costs—make it a worthwhile endeavor for any organization. As threats continue to evolve, Zero Trust provides a flexible and proactive framework to safeguard critical assets and maintain resilience in the face of cyber threats. By embracing Zero Trust, organizations are better positioned to navigate the complex cybersecurity landscape and ensure the protection of their most valuable assets.